Hello There, its been quite a while. But no time like the present to ressurect this blog. Since the beginning of ’21 i have been researching NFC and RFID tags as part of a Cyber Security course. It lead me to finding a hardware device called the Proxmark3 that allowed me to interact with the tags. But i wanted more. Youtube video here
My goal was to write a LUA program that can be executed by the proxmark software. It would sit there listening until it detected a tag, then it would dump the information using that to write a new tag. As this project was for a class, i only had 4 weeks to develop something while learning a new language. I have posted the result (and interations of the build) on my GitHub – https://github.com/somefreak/proxmark-auto-mifare
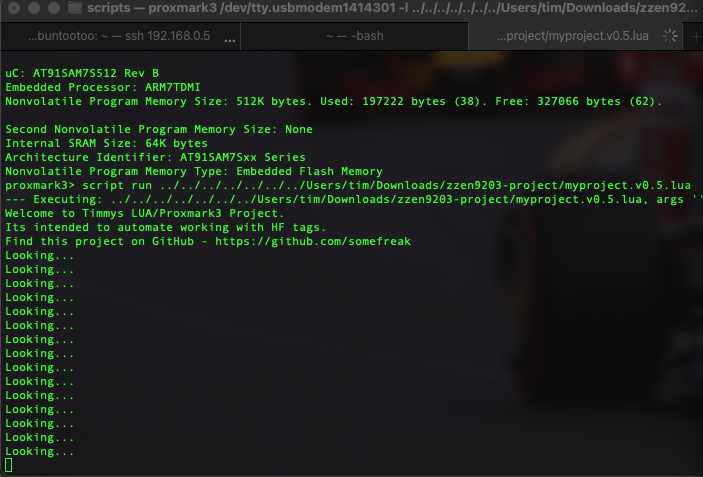
The program i ended up with does not have the entire functionality that i set out to acheive. However i do not count that as failure. My programming skills are amateur level at best, so getting a working program with part functionality feels like i have accomplished something.
Luckily, there are many other LUA proxmark3 projects with more functionality than mine. Here is the references i used while researching and coding my solution:
https://swende.se/blog/Proxmark_Scripting_1.html
https://swende.se/blog/Proxmark_Scripting_2.html
https://stackoverflow.com/questions/1034334/easiest-way-to-make-lua-script-wait-pause-sleep-block-for-a-few-seconds
https://www.tutorialspoint.com/lua/lua_variables.htm
https://www.tutorialspoint.com/lua/lua_repeat_until_loop.htm
https://github.com/Proxmark/proxmark3/blob/master/client/scripts/formatMifare.lua
https://github.com/Proxmark/proxmark3/blob/master/client/scripts/mifare_autopwn.lua
https://github.com/Proxmark/proxmark3/issues/840
https://stackoverflow.com/questions/14629658/lua-repeat-until-seems-to-use-original-value
http://www.troubleshooters.com/codecorn/lua/luaio.htm

Through my research what i have discovered is these tags are just as vulnerable as normal locks with keys. There is no perfect security solution, the only difference between normal locks and lockpicks is the technical barrier of entry is higher for NFC but that doesn’t mean there isn’t digital lock picks out there.